HashiCorp Boundary Enterprise Crack is a comprehensive solution that addresses this challenge by providing a secure, scalable, and easy-to-use remote access platform. Let’s dive into what Boundary Enterprise offers and how it can benefit your organization.
How Does HashiCorp Boundary Enterprise Work?
At its core, Download free Boundary Enterprise is built on the principles of Zero Trust Network Access (ZTNA), which means that no user or device is inherently trusted. Instead, every access request is authenticated, authorized, and encrypted before being granted.
The Boundary Enterprise architecture consists of three main components:
- Controllers: These are the central management points that handle authentication, authorization, and policy enforcement.
- Workers: These are the gateways that facilitate secure connections between clients and target resources.
- Clients: These are the applications or devices used by end-users to initiate secure sessions.
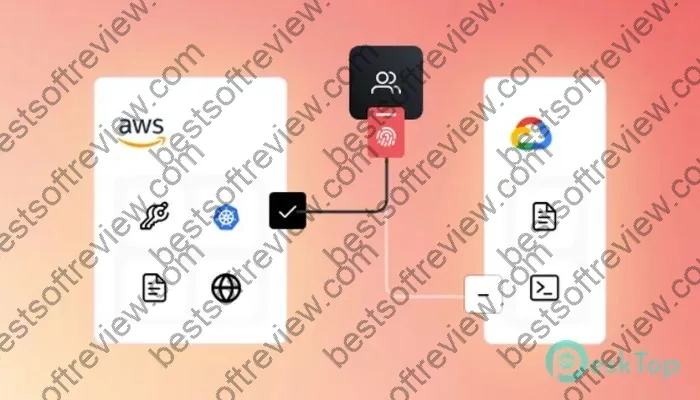
When a user attempts to access a target resource (e.g., a server, database, or application), the client connects to a Boundary worker, which then authenticates the user and authorizes the requested access based on the defined policies. If the request is approved, a secure, encrypted session is established between the client and the target resource.
Key features of Boundary Enterprise include:
- Identity-based Access Control: User access is governed by role-based permissions, ensuring that only authorized individuals can access specific resources.
- Just-in-Time Permissioning: Access is granted on-demand and revoked automatically after the session ends, minimizing the risk of unauthorized access.
- Multi-Cloud Support: Boundary Enterprise seamlessly integrates with major public clouds (AWS, Azure, GCP) and private data centers, enabling secure access across hybrid and multi-cloud environments.
- Secure Networking: All network traffic is encrypted end-to-end using modern cryptographic protocols, protecting against eavesdropping and man-in-the-middle attacks.
Key Benefits of Using Boundary Enterprise
Implementing Boundary Enterprise can provide numerous benefits to organizations, including:
- Enhanced Security: By adhering to the Zero Trust principles, Boundary Enterprise significantly reduces the risk of data breaches and unauthorized access.
- Centralized Access Management: With a centralized control plane, administrators can easily manage and monitor access across the entire organization.
- Simplified Compliance: Boundary Enterprise’s comprehensive audit logs and granular access controls aid in meeting regulatory compliance requirements.
- Improved Productivity: By providing secure access to resources from anywhere, Boundary Enterprise empowers remote teams to work more efficiently.
- Scalability: Boundary Enterprise is designed to scale seamlessly, accommodating the growing needs of modern businesses.
See also:
Setting Up and Using Boundary Enterprise
Boundary Enterprise Crack is available as Docker containers, OCI images, and Helm charts, making it easy to deploy and integrate into existing infrastructure. Let’s go through the key steps involved in setting up and using Boundary Enterprise:
- Installation: First, you’ll need to install the Boundary Enterprise components (controllers, workers, and clients) on your desired platforms.
- Configuration: Next, you’ll need to configure resources such as hosts, host sets, and target resources that you want to secure.
- Access Control: Create users, roles, and bindings to define who has access to which resources. You can integrate with external identity providers like Active Directory or OIDC providers.
- Secure Sessions: End-users can then initiate secure sessions using the Boundary Enterprise clients or SDKs, allowing them to access authorized resources securely.
Integrating with Identity Providers
Boundary Enterprise supports integrating with various identity providers to streamline authentication and authorization processes. Some examples include:
- Active Directory: Use Boundary’s built-in Active Directory auth method to authenticate users against your AD instance.
- LDAP: Authenticate users against an LDAP directory service like OpenLDAP or FreeIPA.
- OIDC Providers: Integrate with popular OIDC providers like Okta, Azure AD, or Google Cloud Identity for seamless single sign-on.
Auditing and Monitoring
Boundary Enterprise provides comprehensive auditing and monitoring capabilities to ensure visibility and compliance:
- Audit Logs: All user activity, including authentication attempts, resource access, and configuration changes, is logged for auditing purposes.
- Monitoring Metrics: Boundary Enterprise exposes various metrics that can be used to monitor the health and performance of the system.
- SIEM Integration: You can integrate Boundary Enterprise with existing Security Information and Event Management (SIEM) tools for centralized logging and analysis.
Boundary Enterprise Use Cases
Boundary Enterprise License Key can be leveraged across various industries and scenarios, including:
- Secure Remote Access for Employees and Contractors: Provide secure access to internal applications, servers, and databases for remote workers and contractors without exposing your network to the internet.
- Third-Party Access for Vendors and Partners: Securely grant access to external parties, such as vendors or partners, without compromising your network security.
- Cloud Infrastructure Access for Operations Teams: Enable your operations teams to securely access and manage cloud resources across multiple cloud providers.
- Database and Internal Application Access for Developers: Allow developers to securely access and test internal databases and applications during the development and testing phases.
- Compliance and Security Best Practices: Implement Boundary Enterprise to adhere to industry compliance standards and security best practices, such as the principle of least privilege and Zero Trust Network Access.
See also:
Boundary Enterprise vs. Alternatives
While there are various VPN and bastion host solutions available, Patch Boundary Enterprise stands out with its comprehensive Zero Trust security model and ease of use. Here’s how it compares to some alternatives:
| Solution | Zero Trust | Multi-Cloud Support | Ease of Use | HSM Integration |
|---|---|---|---|---|
| Boundary Enterprise | ✔️ | ✔️ | ✔️ | ✔️ |
| Traditional VPNs | ❌ | ❌ | ❌ | ❌ |
| Bastion Hosts | ❌ | ✔️ | ❌ | ❌ |
| Other ZTNA Solutions | ✔️ | ✔️ | ❌ | ❌ |
Unlike traditional VPNs, Boundary Enterprise follows the Zero Trust principles, ensuring that no user or device is inherently trusted. It also offers seamless multi-cloud support, making it easy to secure access across hybrid and multi-cloud environments.
Compared to bastion hosts, Boundary Enterprise provides a more comprehensive and scalable solution with its centralized access control, auditing, and monitoring capabilities. It also integrates with Hardware Security Modules (HSMs) for enhanced security.
While other Zero Trust Network Access (ZTNA) solutions exist, Boundary Enterprise stands out with its ease of use, comprehensive documentation, and active community support.
Conclusion
In today’s digital landscape, enabling secure remote access is crucial for maintaining business continuity and productivity. HashiCorp Boundary Enterprise Crack presents a robust and comprehensive solution that leverages the principles of Zero Trust Network Access to secure access across hybrid and multi-cloud environments.
With its centralized access management, granular access controls, comprehensive auditing, and scalability, Boundary Enterprise can benefit organizations of all sizes across various industries. Its ease of use and seamless integration with existing infrastructure make it a compelling choice for organizations seeking to enhance their security posture while enabling secure remote access.
It’s now far simpler to do projects and track information.
The new updates in version the newest are extremely useful.
I appreciate the upgraded workflow.
The program is truly great.
I absolutely enjoy the upgraded workflow.
It’s now a lot more user-friendly to finish tasks and manage content.
I would strongly suggest this software to anyone needing a powerful product.
It’s now a lot more user-friendly to finish tasks and organize content.
The latest features in update the newest are so great.
This software is definitely great.
It’s now a lot more user-friendly to get done jobs and organize content.
The loading times is a lot better compared to the original.
The latest features in update the newest are so helpful.
The loading times is so much faster compared to last year’s release.
I love the new dashboard.
The latest updates in release the latest are incredibly cool.
I would highly recommend this program to anyone wanting a powerful platform.
The responsiveness is a lot improved compared to the previous update.
The loading times is significantly improved compared to last year’s release.
I would absolutely suggest this software to professionals wanting a high-quality platform.
I absolutely enjoy the improved interface.
I would strongly suggest this program to anyone wanting a powerful product.
I would absolutely endorse this application to professionals needing a powerful product.
The program is really great.
I absolutely enjoy the upgraded workflow.
I would highly recommend this application to professionals needing a top-tier product.
I would absolutely suggest this application to professionals wanting a powerful platform.
I appreciate the new interface.
I would highly recommend this software to professionals needing a robust platform.
The speed is significantly faster compared to older versions.
It’s now far more user-friendly to do jobs and organize data.
The performance is a lot better compared to older versions.
I absolutely enjoy the enhanced dashboard.
The software is truly awesome.
The loading times is a lot improved compared to the original.
I absolutely enjoy the new UI design.
The software is absolutely impressive.
The responsiveness is significantly enhanced compared to the previous update.
This tool is really awesome.
I really like the enhanced dashboard.
The software is really impressive.
The speed is so much enhanced compared to older versions.
The recent enhancements in version the latest are so cool.
This program is absolutely great.
The new capabilities in version the newest are really awesome.
I would absolutely recommend this tool to anyone looking for a powerful solution.
It’s now far easier to do projects and organize information.
I absolutely enjoy the upgraded layout.
I would absolutely recommend this application to professionals needing a robust product.
The speed is so much enhanced compared to last year’s release.
I appreciate the new UI design.
It’s now far more user-friendly to do projects and track data.
The performance is a lot improved compared to the original.
The new updates in update the latest are extremely cool.
The application is definitely awesome.
The latest functionalities in release the latest are so awesome.
I would highly endorse this software to professionals wanting a robust product.
The application is absolutely amazing.
The recent enhancements in version the latest are really cool.
I appreciate the enhanced layout.
I would absolutely suggest this software to anyone wanting a powerful product.
The responsiveness is a lot enhanced compared to last year’s release.
The responsiveness is significantly better compared to older versions.
I absolutely enjoy the enhanced layout.
The speed is a lot enhanced compared to the original.
I love the enhanced dashboard.
It’s now much more user-friendly to get done tasks and organize information.
It’s now a lot simpler to finish jobs and organize information.
It’s now much easier to finish work and organize information.
The latest functionalities in version the latest are extremely great.
I love the enhanced UI design.
This platform is really awesome.
The loading times is a lot faster compared to last year’s release.
This software is truly great.
I would definitely recommend this tool to anybody wanting a powerful solution.
It’s now far simpler to complete work and manage content.
It’s now a lot easier to complete tasks and organize content.
The software is truly amazing.
It’s now a lot more user-friendly to get done work and organize content.
I would absolutely recommend this software to anybody wanting a robust solution.
This application is absolutely amazing.
This platform is definitely awesome.
I would strongly suggest this tool to anyone looking for a high-quality solution.
I love the new interface.
I appreciate the improved layout.
I would strongly suggest this program to professionals wanting a powerful platform.
This software is absolutely fantastic.